Spera’s technology allows them to fill in what have been cracks in identity access management, which they view as highly complementary to existing IAM and IGA vendors.
 Today Spera, an Israeli cybersecurity startup that provides what they term Identity Security Posture Management [ISPM] has announced $10 million in seed funding. The funding round is led by YL Ventures, which specializes in Israel tech startups. It also involves investors with pedigrees from companies which include Google, Palo Alto Networks, Akamai, Zendesk, and Zscaler.
Today Spera, an Israeli cybersecurity startup that provides what they term Identity Security Posture Management [ISPM] has announced $10 million in seed funding. The funding round is led by YL Ventures, which specializes in Israel tech startups. It also involves investors with pedigrees from companies which include Google, Palo Alto Networks, Akamai, Zendesk, and Zscaler.
Spera identifies what they do as Identity Security Posture Management, a proprietary term, that provides a more precise definition of their focus.
“The formal Garner category is Identity Threat Detection and Response, which was created in 2022,” said Dor Fledel, Spera’s CEO. “We think that the category is too broad, and that ISPM, which is our own innovation, is part of it.”
“In the problem of controlling identity and access sprawl, how can security teams measure risk and IT posture management,” Fledel asked. “Today, that measurement is not really handled through products. It’s something that is between the cracks. Traditional IAM vendors like Okta provide some of it. IGA vendors provide some of it. But the area where the biggest risk is mapped is done by a lot of do-it-yourself work.

The Spera team
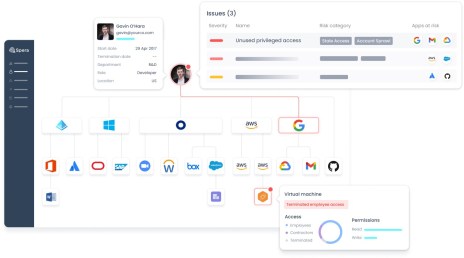
“Our core strength is inventory of access permissions, which are accessed through the Spera Access Graph,” Fledel said. “Another key innovation is our user correlation. We have found outliers of almost every security program. This provides a significant intellectual property advantage for us over competitors.” The platform provides real-time, continuously updated, risk and context-based inventory of identities and access across cloud and on-prem environments, which are assessed for security teams with critical granular insights so that they can remediate and prevent identity-driven attacks.
So why hasn’t this been addressed previously, if it’s so important? Fledel said there are two reasons, one of which is conceptual and the other is technical.
“The conceptual reason is that while existing IAM solutions are in compliance, they serve an operational product. Okta for example adds and removes permissions. But while organizations now want to see the specific risks to an organization, Okta and the IGA vendors don’t have a risk dashboard. Gartner is now pushing security-first identity.”
Fledel said that the technical issues needed to deal with this issue were quite sophisticated, that it was not simply a matter of putting together basic vendor integrations.
“We integrate into the entire identity stack and core applications,” he stated. “It is very complicated work, which analyzes the actual action to understand who is doing what. It requires very deep integration with like of AWS and Salesforce.”
Spera sells to larger customers, but their market is actually broader than that.
“Organizations which range in size from 500-50,000 have growing problems with IAM as well,” Fledel said. “It’s not just large enterprises. We have fast growing startups as customers too.” Contractors, machine identity and Privileged Accounts are three distinct customer sweet spots.
“Even with two or three integrations, we provide value,” Fledel stated. “We closed one deal with three integrations.”
Fledel views the IAM and IGA players in the market as potential partners rather than competitors.
“They are pure co-operators,” he said. “If not for the secure sign-on revolution, we would not be able to operate. We do want to be the next Okta. We are always expanding our integration base, and expect to have hundreds of these strategic integrations in the next few years.”
Spera’s long term plans are channel, but even at this early stage, they have already begun working with partners.
“The channel is highly important to us,” Fledel said. “Zero trust implementations tend to be channel focused. We have already started engaging with some partners and are already deep with one of them.”
Fledel identified their ideal partner type as system integrators and those who create those implementation around security that are focused on Zero Trust and IAM.
“In addition to providing our strong ROI, one of our greatest values is risk assessment – knowing where the gaps are,” he stated. “This is something that we see as highly complementary to channel value.”










